Positive Technologies, an industry leader in result-driven cybersecurity, has analyzed cyber threats relevant to the public sector from 2022 through the first half of 2024. The study highlights regions with high levels of attack activity: Russia, countries in Asia (33%), Africa (12%), and North America (12%) are of the greatest interest to cybercriminals.
Government institutions in Asia, in particular, are attractive to attackers for a number of reasons. Asian countries have become leaders in technological innovation in recent years, and while the public sector is also undergoing a digital transformation, its cybersecurity is still not at an adequate level. In addition, the economic competition and trade wars continue in cyberspace, taking the form of carefully planned and targeted attacks on government agencies.
Nearly half of all successful cyberattacks (48%) during the studied period were targeted, and most often they resulted in data breaches (62% of cases). The attacks were carried out by highly skilled APT groups and hacktivists. The most frequently stolen information was personal data (33%) and intellectual property (30%).
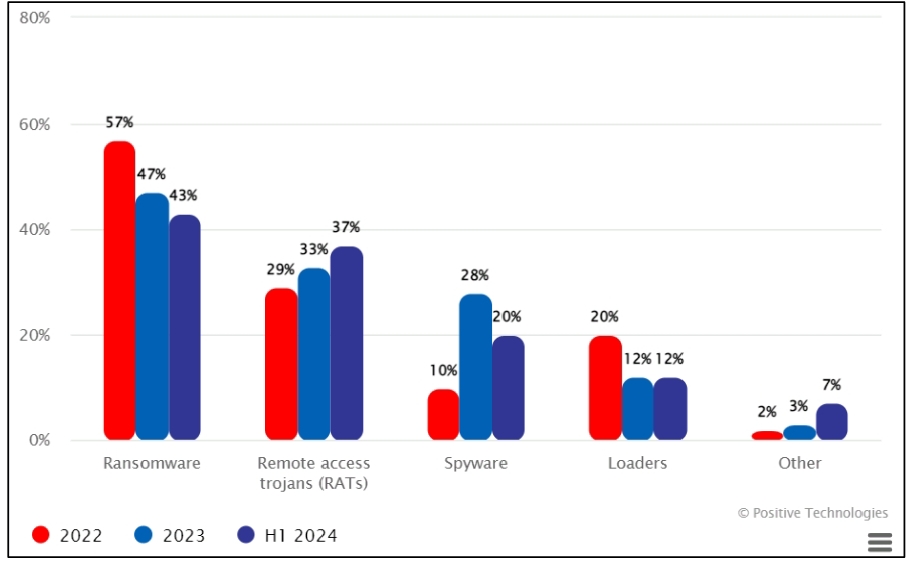
According to the report, ransomware remains the most common type of malware used in attacks. At the same time, experts note their declining popularity in the public sector: in the first six months of 2024, the percentage of successful ransomware incidents decreased by 4% compared to 2023 and 14% compared to 2022.
Government institutions, which typically refuse to pay ransom for stolen data, are nonetheless under threat, warns Positive Technologies. Attackers target them not so much for financial gain, but with the intent to disrupt government systems and steal or destroy confidential data. The experts also link this choice of targets to the large number of employees who actively use email and other communication tools at work: this creates numerous entry points to the infrastructure of government agencies.
The most common consequence of successful attacks is the disruption of core operations (48% of incidents), followed by the leakage of confidential information (41%). The analysts observed a continuous increase in data breaches, which accounted for 37% cases in 2022, 41% in 2023, and 48% in the first half of 2024.
The primary targets used to infiltrate government networks were computers, servers, and network equipment: according to Positive Technologies, 80% of successful attacks were directed at them. In nearly half of the incidents (47%) examined in the study, attackers used social engineering and relied on the human factor to deceive their victims. In 56% of successful attacks, malware was also employed.
The experts warn that the popularity of the latter method is steadily increasing, accounting for 48% of incidents in 2022, 57% in 2023, and 68% in the first half of 2024. This dynamic is mainly driven by the simplicity and effectiveness of malware as an attack tool. It is also supported by an active darknet market where threat actors can rent or purchase off-the-shelf malware, or even commission a customized version.
The public sector is the most attractive target for APT groups. APT attacks most frequently employ malware (83% of incidents), which is generally either primarily remote access trojans (65% of cases) or spyware (35% of cases). Additionally, cybercriminals purchase or exchange credentials on the dark web to use them for accessing compromised devices.
Positive Technologies says an analysis of darknet marketplaces revealed that one in every six ads offered access to the infrastructure of compromised government organizations. The price ranged from twenty to several thousand USD for high-privilege access. In one-third of the ads, it revealed that the price was not specified: this means that the parties negotiated it privately. To effectively counter complex cyberthreats, companies can use MaxPatrol O2, an autopilot for result-driven cybersecurity. This metaproduct, renowned for successful detection of attacks carried out by world-class hacker groups, is already being used by several government agencies.
“The more digitally advanced a government is, the more it depends on technology. The colossal volume of confidential data stored in government IT systems, along with the critical significance of uninterrupted operations of government agencies, make this sector an attractive target for all kinds of threat actors: professional APT groups, skilled lone attackers, and hacktivists. Our studies show that government institutions have topped the list of the most successfully attacked sectors over the past six years,” says Anna Vyatkina, Information Security Analyst at Positive Technologies.
“To improve their security posture, government agencies need to follow the result-driven cybersecurity approach. First, identify potential non-tolerable events (events that result from a cyberattack and prevent you from achieving your operational and/or strategic goals, or lead to significant disruption of your core activities) and the main potential targets among your IT assets. After that, undergo a cyber transformation, which includes hardening of the IT infrastructure, training of employees in cybersecurity basics, establishment of incident monitoring and response, and running security assessments. Finally, maintain and confirm cyber resilience by means of cyber exercises and bug bounty programs.” Vyatkina explained
According to Positive Technologies, the importance of pursuing the result-driven cybersecurity approach in the public sector is dictated by the dangerous consequences of cyberattacks: an attack on one government agency can affect other agencies, the entire country, and its citizens. For example, the theft of users’ personal data in a cyberattack on a government institution can lead to unauthorized access to information resources of other government-owned or commercial organizations.