Part 2 of 2.
Rising Android SMS Attacks in Kenya
Kenya is facing a significant surge in Android SMS attacks, with an average of 1000 attacks occurring daily. This alarming trend poses severe implications for both individual users and organizational networks across the country.

The implications of these daily attacks are far-reaching and potentially devasting. Android SMS attacks can lead to unauthorized access to personal and sensitive information, financial data theft, and even the compromise of critical systems and infrastructure.
Given the escalating frequency and sophistication of Android SMS attacks in Kenya, proactive cybersecurity measures and heightened vigilance are essential to safeguard personal and organizational data, protect digital assets, and preserve the integrity of the country’s digital ecosystem.
Compromised Websites

In the heart of Kenya’s bustling digital landscape, over 100 websites fall victim to cyber compromises daily. This alarming trend not only jeopardizes the online presence of businesses but also undermines the trust and integrity of Kenya’s digital economy., is witnessing a surge in cyber-attacks that target businesses of all sizes. From e-commerce platforms to financial institutions, no sector is immune to the perils of cyber vulnerabilities.
Safeguarding sensitive information, fortifying digital infrastructures, and implementing proactive threat detection mechanisms are essential steps in mitigating cyber risks.
Embracing a cybersecurity-first mindset is not just a matter of compliance; it’s a strategic imperative for businesses looking to thrive in the digital age. By prioritizing cybersecurity investments, organizations can safeguard their operations, protect their customers, and bolster the resilience of Kenya’s digital ecosystem.
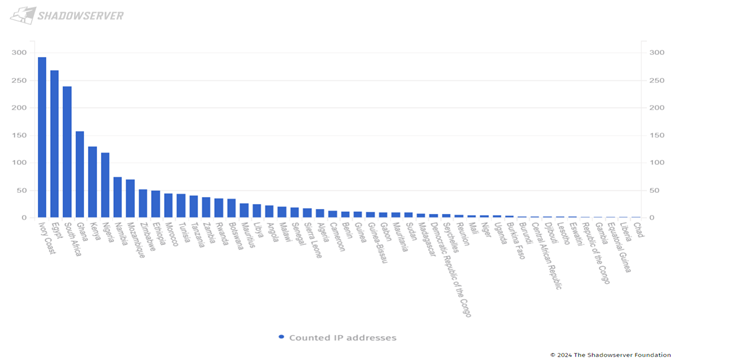
Hardware implant attacks

The graph below illustrates a concerning trend of escalating attacks on computer systems, notably highlighting the prevalence of hardware implant attacks.
These sophisticated tactics are being deployed by malicious actors to manipulate vulnerable IoT devices, compelling them to establish static IP addresses that serve as backdoors for unauthorized remote access. Notably, Kenya is experiencing a daily average of 250 such attacks. This insidious form of cyber threat demands heightened vigilance and robust cybersecurity protocols to safeguard against unauthorized intrusions.

Decoding CVE Scores: A Crucial Guide to understanding Cyber Vulnerabilities
CVE, short for Common Vulnerabilities and Exposures, provides a standardized method for identifying and categorizing vulnerabilities in software and hardware systems. These vulnerabilities are assigned unique identifiers known as CVE IDs, along with corresponding scores that gauge the severity of the potential threat posed. CVE scores, typically ranging from 0 to 10, are crucial indicators of the level of risk associated with a particular vulnerability.
The scoring system considers factors such as exploitability, impact, and complexity, offering businesses a clear insight into the urgency and severity of addressing the identified vulnerabilities. For companies seeking to fortify their cybersecurity defenses, leveraging CVE scores as a guiding metric is instrumental in prioritizing remediation efforts and mitigating potential risks. By monitoring CVE databases and charts, businesses can gain visibility into the vulnerabilities present in their digital ecosystem and assess the criticality of each identified threat.

Why Every Business Needs Cybersecurity?
Most Kenyan businesses do not understand their role in the cybersecurity ecosystem in Kenya. Companies lack information, knowledge, and resources to defend their assets. There is an urgent need for information sharing amongst businesses. Companies need to understand their supply chain cybersecurity risk associated with their daily business interactions with third parties. Companies are not reporting breaches to the relevant authorities because they fear reputational damage, this would further complicate the cybersecurity posture of Kenya in the long run.
It is very important for CEOs to priority cybersecurity in their overall business strategy. The global cyber threat landscape is changing, threat actors are getting more sophisticated every day, companies must analyze their assets to see which asset exposure to attack will critically impact on the business. This is true as no company will be able to protect all its assets. Companies must strive to continually improve their company cybersecurity posture as is good for business. Executives should lead a Top-Down-Down-Up cybersecurity risk management and cybersecurity strategy; this would help identify all their business assets and assign Asset Value (AV) to all the assets. With knowledge of the all the business assets the CEO and team can now see the expected loss to the company if these assets are exposed to cyber-attack.

The business calculation for a loss because of a cyber- attack
ALE = SLE x ARO
ARO= Annual rate of occurrence.
ALE = The Annualized loss Expectancy
SLE = AV x EF * AV= Asset Value, EF = Exposure factor
The importance of proactive cybersecurity measures in safeguarding sensitive data and maintaining business continuity.
Developing a cyber security strategy keeps a business in a state of readiness, which means the business can swiftly respond and defend itself from breaches when it occurs and restore the business back to normal quicker.
As mentioned earlier it is hard for a business to defend all its assets against attacks, and because organizations are at different levels of cyber maturity, the focus should be on those assets whose exposure would have a critical impact on the business operation.
Cyber Threat monitoring plan gives businesses the playbook to identify, protect, detect, respond, and recover from cyber security incidence. This helps the company develop a respond to the threat, communication to those affected by the breach and notification to regulators. This will help in the development of Kenya cyber security ecosystem compliance practices.
Cyber Security Framework
There are several risks management frameworks which corporations can use to build a robust cyber security program. The models listed below are only an overview.
NIST Cyber Security Framework
Teir 1: Partial
Risk Management Process: No established formal process for risk management, risk is approached in and ad hoc basis no priority.
Organizational Adoption: There is an overall lack of cyber awareness of business cybersecurity risk and no information sharing within the organisation.
External Participation: The organisation doesn’t understand its larger role in the ecosystem and does not collaborate or share information.
Teir 2: Risk Informed
Risk Management Process: There are approved practices but are not shared across the organisation, risk is managed by organisation objectives.
Organizational Adoption: The business has some cybersecurity awareness, but no risk management plan. There is some kind of information sharing.
External Participation: The organisation has some understanding of its larger role in the ecosystem but has limited collaboration or sharing of information.
Teir 3: Repeatable
Risk Management Process: Formalized practices and cyber security risk are managed regularly against business requirements and a changing threat environment.
Organizational Adoption: There is an organizational wide approach to managing cyber security risk, accurate monitoring and communicating of cyber security risk between staff.
External Participation: The organisation understands its larger role in the ecosystem and collaborates and shares information regularly.
Teir 4: Adaptive
Risk Management Process: There are adaptive practices with continuous improvement, incorporating advanced cyber security practices and technologies to combat sophisticated threats.
Organizational Adoption: There is an organizational wide approach using risk-informed polices and a clear understanding of the relationship between cyber security risk and business objectives.
External Participation: The organisation understands its larger role in the ecosystem and receives, generates, reviews, and prioritizes information that gives a continuous analysis of risk and threats, using real-time and near-real-time information to act upon risks. It communicates proactively to develop formal and informal supply chain agreements.

ASD Essential Eight
Developed by the Australian Signal Directorate (ASD) to help organisation protect their systems from attacks.
- Application Control
- Patch application.
- Configure Microsoft Office macro settings.
- User application hardening
- Restrict administrative privileges.
- Patch operating systems.
- Multifactor authentication
- Daily backups.
The maturity levels are defined as follows:
Maturity level one: Partly aligned with the intent of the mitigation strategy.
Maturity level two: Mostly aligned with the intent of the mitigation strategy.
Maturity level three: Fully aligned with the intent of the mitigation strategy.
Click here to read Part 1: Cyber Threat Landscape in Kenya: Trends and Solution
Obase Mandi Manga is the Cyber Security Engineer, HackProof Hub. www.hackproofhub.au Email: mandi@hackproofhub.au





